机器 SID 重复神话(以及 Sysprep 为何重要)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
发布于 2019 年 6 月 26 日 11:58 PM 105,000 次观看
首次发布于 2009 年 11 月 3 日在 TechNet 上
On November 3 2009, Sysinternals retired
NewSID
, a utility that changes a computers
machine Security Identifier
(machine SID). I wrote NewSID in 1997 (its original name was NTSID) because the only tool available at the time for changing machine SIDs was the Microsoft
Sysprep
tool, and Sysprep doesn’t support changing the SIDs of computers that have applications installed. A machine SID is a unique identifier generated by Windows Setup that Windows uses as the basis for the SIDs for administrator-defined local accounts and groups. After a user logs on to a system, they are represented by their account and group SIDs with respect to object authorization (permissions checks). If two machines have the same machine SID, then accounts or groups on those systems might have the same SID. It’s therefore obvious that having multiple computers with the same machine SID on a network poses a security risk, right? At least that’s been the conventional wisdom.
2009 年 11 月 3 日,Sysinternals 停用了 NewSID,这是一个更改计算机机器安全标识符(机器 SID)的实用程序。我在 1997 年编写了 NewSID(它的原始名称是 NTSID),因为当时唯一可用的更改计算机 SID 的工具是 Microsoft Sysprep 工具,而 Sysprep 不支持更改安装了应用程序的计算机的 SID。计算机 SID 是由 Windows 安装程序生成的唯一标识符,Windows 将其用作管理员定义的本地帐户和组的 SID 的基础。用户登录到系统后,他们由其帐户和组 SID 代表对象授权(权限检查)。如果两台计算机具有相同的计算机 SID,则这些系统上的帐户或组可能具有相同的 SID。因此,很明显,网络上有多台具有相同计算机 SID 的计算机会带来安全风险,对吗?至少这是传统观点。
The reason that I began considering NewSID for retirement is that, although people generally reported success with it on Windows Vista, I hadn’t fully tested it myself and I got occasional reports that some Windows component would fail after NewSID was used. When I set out to look into the reports I took a step back to understand how duplicate SIDs could cause problems, a belief that I had taken on faith like everyone else. The more I thought about it, the more I became convinced that machine SID duplication – having multiple computers with the same machine SID – doesn’t pose any problem, security or otherwise. I took my conclusion to the Windows security and deployment teams and no one could come up with a scenario where two systems with the same machine SID, whether in a Workgroup or a Domain, would cause an issue. At that point the decision to retire NewSID became obvious.
我开始考虑停用 NewSID 的原因是,尽管人们普遍报告在 Windows Vista 上使用 NewSID 取得了成功,但我自己并没有对其进行全面测试,并且偶尔收到报告称使用 NewSID 后某些 Windows 组件会出现故障。当我开始查看这些报告时,我退后一步,了解重复的 SID 会如何导致问题,这是我和其他人一样坚信的信念。我想得越多,就越相信机器 SID 重复(多台计算机具有相同的机器 SID)不会造成任何问题、安全性或其他问题。我向 Windows 安全和部署团队得出结论,没有人能想到这样一种情况:具有相同计算机 SID 的两个系统(无论是在工作组还是在域中)都会导致问题。那时,退出 NewSID 的决定就变得显而易见了。
I realize that the news that it’s okay to have duplicate machine SIDs comes as a surprise to many, especially since changing SIDs on imaged systems has been a fundamental principle of image deployment since Windows NT’s inception. This blog post debunks the myth with facts by first describing the machine SID, explaining how Windows uses SIDs, and then showing that - with one exception - Windows never exposes a machine SID outside its computer, proving that it’s okay to have systems with the same machine SID. Note that Sysprep resets other machine-specific state that, if duplicated, can cause problems for certain applications like Windows Server Update Services (WSUS), so MIcrosoft's support policy will still require cloned systems to be made unique with Sysprep.
我意识到,可以有重复的计算机 SID 的消息让许多人感到惊讶,特别是因为自 Windows NT 诞生以来,更改映像系统上的 SID 一直是映像部署的基本原则。这篇博文用事实揭穿了这一神话,首先描述了机器 SID,解释了 Windows 如何使用 SID,然后表明(除了一个例外)Windows 绝不会在其计算机之外公开机器 SID,从而证明系统可以具有相同的 SID机器 SID。请注意,Sysprep 会重置其他特定于计算机的状态,如果重复,可能会导致 Windows Server Update Services (WSUS) 等某些应用程序出现问题,因此 Microsoft 的支持策略仍然要求通过 Sysprep 使克隆系统变得唯一。
SIDs SID
Windows uses SIDs to represent not just machines, but all
security principals.
Security principals include machines, domain computer accounts, users and security groups. Names are simply user-friendly representations for SIDs, allowing you to rename an account and not have to update access control lists (ACLs) that reference the account to reflect the change. A SID is a variable-length numeric value that consists of a structure revision number, a 48-bit identifier authority value, and a variable number of 32-bit subauthority or relative identifier (RID) values. The authority value identifies the agent that issued the SID, and this agent is typically a Windows local system or a domain. Subauthority values identify trustees relative to the issuing authority, and RIDs are simply a way for Windows to create unique SIDs based on a common base SID.
Windows 使用 SID 不仅代表机器,还代表所有安全主体。安全主体包括计算机、域计算机帐户、用户和安全组。名称只是 SID 的用户友好表示形式,允许您重命名帐户,而不必更新引用该帐户的访问控制列表 (ACL) 以反映更改。 SID 是一个可变长度的数值,由结构修订号、48 位标识符权限值和可变数量的 32 位子权限或相对标识符 (RID) 值组成。权限值标识发出 SID 的代理,该代理通常是 Windows 本地系统或域。子权限值标识相对于颁发机构的受托者,而 RID 只是 Windows 基于公共基本 SID 创建唯一 SID 的一种方式。
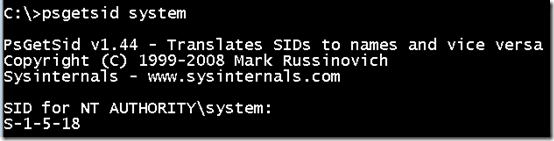
You can use the Sysinternals
PsGetSid
tool to view a machine’s SID by running it with no command-line arguments:
您可以使用 Sysinternals PsGetSid 工具通过在不使用命令行参数的情况下运行该工具来查看计算机的 SID:
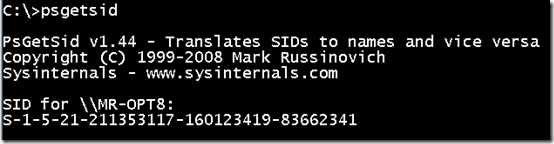
Here, the revision number is 1, the authority is 5, and there are four subauthority values. At one point during the design of Windows NT, the machine SID might have been used for network identification, so in order to assure uniqueness, the SID that Setup generates has one fixed subauthority value (21) and three randomly-generated subauthority values (the numbers following “S-1-5-21” in the output).
这里,修订号为1,权限为5,子权限值有4个。在 Windows NT 的设计过程中,机器 SID 可能曾被用于网络标识,因此为了保证唯一性,安装程序生成的 SID 具有一个固定的子权限值 (21) 和三个随机生成的子权限值(输出中“S-1-5-21”后面的数字)。
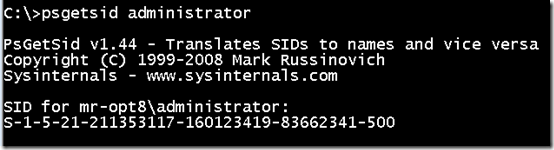
Even before you create the first user account on a system, Windows defines several built-in users and groups, including the Administrator and Guest accounts. Instead of generating new random SIDs for these accounts, Windows ensures their uniqueness by simply appending a per-account unique number, called a
Relative Identifier
(RID), to the machine SID. The RIDs for these initial accounts are predefined, so the Administrator user always has a RID of 500:
即使在系统上创建第一个用户帐户之前,Windows 也会定义多个内置用户和组,包括管理员和来宾帐户。 Windows 不会为这些帐户生成新的随机 SID,而是通过简单地将每个帐户的唯一编号(称为相对标识符 (RID))附加到计算机 SID 来确保其唯一性。这些初始帐户的 RID 是预定义的,因此管理员用户的 RID 始终为 500:
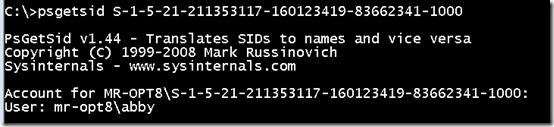
After installation, Windows assigns new local user and group accounts with RIDs starting at 1000. You can use PsGetSid to view the name of the account for a specified SID, and here you can see that the local SID that has a RID of 1000 is for the Abby account, the name of the administrator account Windows prompted me to name during setup:
安装完成后,Windows 会分配新的本地用户和组帐户,RID 从 1000 开始。您可以使用 PsGetSid 查看指定 SID 的帐户名称,在这里可以看到 RID 为 1000 的本地 SID 用于Abby 帐户,管理员帐户的名称 Windows 在安装过程中提示我命名:
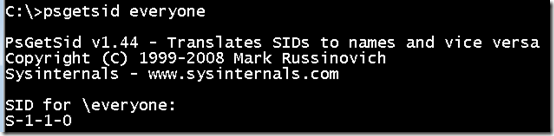
In addition to these dynamically created SIDs, Windows defines a number of accounts that always have predefined SIDs, not just RIDs. One example is the Everyone group, which has the SID S-1-1-0 on every Windows system:
除了这些动态创建的 SID 之外,Windows 还定义了许多始终具有预定义 SID(而不仅仅是 RID)的帐户。一个例子是Everyone组,它在每个Windows系统上都有SID S-1-1-0:
Another example, is the Local System account (System), which is the account in which several system processes like Session Manager (Smss.exe), the Service Control Manager (Services.exe) and Winlogon (Winlogon.exe) run:
另一个例子是本地系统帐户(System),它是运行会话管理器(Smss.exe)、服务控制管理器(Services.exe)和Winlogon(Winlogon.exe)等多个系统进程的帐户:
SIDs and Access Control Lists
SID 和访问控制列表
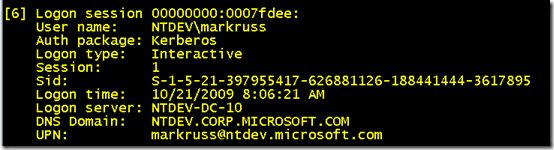
When an account logs on to a Windows system, the Local Security Authority Subsystem (LSASS -Lsass.exe) creates a logon session and a
token
for the session. A token is a data structure the Windows kernel defines to represent the account and it contains the account’s SID, the SIDs of the groups that the account belongs to at the time it authenticated, and the security privileges assigned to the account and the groups. When the last token that references a logon session is deleted, LSASS deletes the logon session and the user is considered logged off. Here you can see my interactive logon session, displayed with the Sysinternals
LogonSessions
utility:
当帐户登录到 Windows 系统时,本地安全机构子系统 (LSASS -Lsass.exe) 创建登录会话和该会话的令牌。令牌是 Windows 内核定义的用于表示帐户的数据结构,它包含帐户的 SID、帐户在进行身份验证时所属组的 SID 以及分配给帐户和组的安全权限。当引用登录会话的最后一个令牌被删除时,LSASS 会删除登录会话,并且用户将被视为已注销。在这里您可以看到我的交互式登录会话,使用 Sysinternals LogonSessions 实用程序显示:
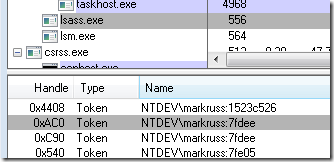
And here you can see a token Lsass has created for the session in Process Explorer’s handle view. Note that number following the account name, 7fdee, matches the logon session ID shown by LogonSessions:
在这里,您可以在 Process Explorer 的句柄视图中看到 Lsass 为会话创建的令牌。请注意,帐户名后面的数字 7fdee 与 LogonSessions 显示的登录会话 ID 匹配:
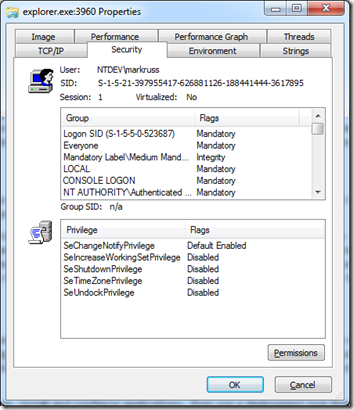
By default, processes inherit a copy of their parent process’s token. Every process running in my interactive session, for example, has a copy of the token that they inherited originally from the Userinit.exe process, the process Winlogon creates as the first of any interactive logon. You can view the contents of a process’s token by double-clicking on the process in
Process Explorer
and switching to the Security page of the process properties dialog:
默认情况下,进程继承其父进程令牌的副本。例如,在我的交互式会话中运行的每个进程都有一个令牌的副本,该令牌最初是从 Userinit.exe 进程继承的,该进程是 Winlogon 作为任何交互式登录的第一个创建的进程。您可以通过双击 Process Explorer 中的进程并切换到进程属性对话框的“安全”页面来查看进程令牌的内容:
When one of my processes opens an operating system object, like a file or registry key, the security subsystem executes a permission check that evaluates entries in the object’s access control list (ACL) that reference a SID included in the process’s token.
当我的某个进程打开一个操作系统对象(例如文件或注册表项)时,安全子系统会执行权限检查,评估该对象的访问控制列表 (ACL) 中引用进程令牌中包含的 SID 的条目。
A similar check happens for remote logon sessions, which are the kind created by a “net use” of a remote computer’s share. To successfully connect to a share you must authenticate to the remote system with an account known to that system. If the computer is part of a Workgroup, then the credentials you specify must be for a local account on the remote system; for a Domain-joined system, the credentials can be for a remote system’s local account or a Domain account. When you access a file on the share, the file server driver on that system uses the token from the logon session for the permission check, leveraging a mechanism called
impersonation
.
类似的检查也会发生在远程登录会话上,远程登录会话是由远程计算机共享的“网络使用”创建的类型。要成功连接到共享,您必须使用远程系统已知的帐户进行身份验证。如果计算机是工作组的一部分,则您指定的凭据必须用于远程系统上的本地帐户;对于加入域的系统,凭据可以是远程系统的本地帐户或域帐户。当您访问共享上的文件时,该系统上的文件服务器驱动程序使用登录会话中的令牌进行权限检查,并利用称为模拟的机制。
SID Duplication SID重复
The Microsoft-supported way to create a Windows installation that’s ready for deployment to a group of computers is to install Windows on a reference computer and prepare the system for cloning by running the Sysprep tool. This is called
generalizing
the image, because when you boot an image created using this process, Sysprep
specializes
the installation by generating a new machine SID, triggering plug-and-play hardware detection, resetting the product activation clock, and setting other configuration data like the new computer name.
Microsoft 支持的创建可部署到一组计算机的 Windows 安装的方法是在参考计算机上安装 Windows,并通过运行 Sysprep 工具准备系统以进行克隆。这称为通用化映像,因为当您启动使用此过程创建的映像时,Sysprep 通过生成新计算机 SID、触发即插即用硬件检测、重置产品激活时钟以及设置其他配置数据(例如新的计算机名称。
However, some IT administrators install Windows on one of their systems, install and configure applications, then use deployment tools that don’t reset the SIDs of the copies of the Windows installations. The best practice up to now has been to run a SID-resetting utility like NewSID to change SIDs. These utilities generate a new machine SID, try to find all the locations on a system, including all the file system and registry ACLs, that contain copies of the machine SID, and update them to the new SID. The reason that Microsoft doesn’t support systems modified in this way is that, unlike Sysprep, these tools don’t necessarily know about all the places where Windows stashes away references to the machine SID. The reliability and security of a system that has a mix of the old and new machine SID can’t be guaranteed.
然而,一些 IT 管理员在其系统之一上安装 Windows,安装和配置应用程序,然后使用不会重置 Windows 安装副本的 SID 的部署工具。迄今为止的最佳实践是运行 SID 重置实用程序(例如 NewSID)来更改 SID。这些实用程序生成新的计算机 SID,尝试查找系统上包含计算机 SID 副本的所有位置(包括所有文件系统和注册表 ACL),并将它们更新为新的 SID。 Microsoft 不支持以这种方式修改的系统的原因是,与 Sysprep 不同,这些工具不一定知道 Windows 隐藏对计算机 SID 的引用的所有位置。混合使用新旧机器 SID 的系统的可靠性和安全性无法得到保证。
So is having multiple computers with the same machine SID a problem? The only way it would be is if Windows ever references the machine SIDs of other computers. For example, if when you connected to a remote system, the local machine SID was transmitted to the remote one and used in permissions checks, duplicate SIDs would pose a security problem because the remote system wouldn’t be able to distinguish the SID of the inbound remote account from a local account with the same SID (where the SIDs of both accounts have the same machine SID as their base and the same RID). However as we reviewed, Windows doesn’t allow you to authenticate to another computer using an account known only to the local computer. Instead, you have to specify credentials for either an account local to the remote system or to a Domain account for a Domain the remote computer trusts. The remote computer retrieves the SIDs for a local account from its own Security Accounts Database (SAM) and for a Domain account from the Active Directory database on a Domain Controller (DC). The remote computer never references the machine SID of the connecting computer.
那么多台计算机具有相同的机器 SID 会出现问题吗?唯一的方法是 Windows 引用其他计算机的计算机 SID。例如,如果当您连接到远程系统时,本地计算机 SID 被传输到远程系统并用于权限检查,则重复的 SID 会造成安全问题,因为远程系统将无法区分远程系统的 SID。来自具有相同 SID 的本地帐户的入站远程帐户(其中两个帐户的 SID 具有相同的计算机 SID 作为其基础和相同的 RID)。然而,正如我们所评论的,Windows 不允许您使用仅本地计算机已知的帐户向另一台计算机进行身份验证。相反,您必须指定远程系统本地帐户或远程计算机信任的域的域帐户的凭据。远程计算机从其自己的安全帐户数据库 (SAM) 检索本地帐户的 SID,并从域控制器 (DC) 上的 Active Directory 数据库检索域帐户的 SID。远程计算机从不引用连接计算机的计算机 SID。
In other words, it’s not the SID that ultimately gates access to a computer, but an account’s user name and password: simply knowing the SID of an account on a remote system doesn’t allow you access to the computer or any resources on it. As further evidence that a SID isn’t sufficient, remember that built-in accounts like the Local System account have the same SID on every computer, something that would be a major security hole if it was.
换句话说,最终控制对计算机的访问的不是 SID,而是帐户的用户名和密码:仅仅知道远程系统上帐户的 SID 并不允许您访问计算机或其上的任何资源。作为 SID 不够充分的进一步证据,请记住,本地系统帐户等内置帐户在每台计算机上都具有相同的 SID,如果是这样,这将是一个主要的安全漏洞。
As I said earlier, there’s one exception to rule, and that’s DCs themselves. Every Domain has a unique
Domain SID
that’s the machine SID of the system that became the Domain’s first DC,
and all machine SIDs for the Domain’s DCs match the Domain SID. So in some sense, that’s a case where machine SIDs do get referenced by other computers. That means that Domain member computers cannot have the same machine SID as that of the DCs and therefore Domain. However, like member computers, each DC also has a computer account in the Domain, and that’s the identity they have when they authenticate to remote systems.
正如我之前所说,有一个例外需要遵守,那就是 DC 本身。每个域都有一个唯一的域 SID,它是成为域的第一个 DC 的系统的机器 SID,并且该域的 DC 的所有机器 SID 都与域 SID 匹配。因此,从某种意义上说,这是机器 SID 确实被其他计算机引用的情况。这意味着域成员计算机不能具有与 DC 和域相同的计算机 SID。但是,与成员计算机一样,每个 DC 在域中也有一个计算机帐户,这是它们向远程系统进行身份验证时所拥有的身份。
Some articles on SID duplication, including this
KB article
, warn that if multiple computers have the same SID, that resources on removable media like an NTFS-formatted firewire disk can’t be secured to a local account. What they fail to mention is that permissions on removable media provide no security regardless, because a user can connect them to computers running operating systems that don’t honor NTFS permissions. Moreover, removable media tend to have default permissions that grant access to well-known SIDs, such as to the Administrators group, which are the same on all systems. That’s the fundamental rule of physical security and why Windows 7 introduced Bitlocker-to-Go, which enables you to encrypt removable storage.
一些有关 SID 复制的文章(包括这篇知识库文章)警告说,如果多台计算机具有相同的 SID,则无法将可移动媒体(如 NTFS 格式的火线磁盘)上的资源保护到本地帐户。他们没有提到的是,可移动媒体上的权限无论如何都不会提供安全性,因为用户可以将它们连接到运行不支持 NTFS 权限的操作系统的计算机。此外,可移动媒体往往具有默认权限,授予对众所周知的 SID 的访问权限,例如管理员组,这在所有系统上都是相同的。这是物理安全的基本规则,也是 Windows 7 引入 Bitlocker-to-Go 的原因,它使您能够加密可移动存储。
The final case where SID duplication would be an issue is if a distributed application used machine SIDs to uniquely identify computers. No Microsoft software does so and using the machine SID in that way doesn’t work just for the fact that all DC’s have the same machine SID. Software that relies on unique computer identities either uses computer names or computer Domain SIDs (the SID of the computer accounts in the Domain).
SID 重复成为问题的最后一种情况是分布式应用程序使用计算机 SID 来唯一标识计算机。没有 Microsoft 软件这样做,并且以这种方式使用计算机 SID 并不能仅仅因为所有 DC 都具有相同的计算机 SID。依赖唯一计算机标识的软件使用计算机名称或计算机域 SID(域中计算机帐户的 SID)。
The New Best Practice
新的最佳实践
It’s a little surprising that the SID duplication issue has gone unquestioned for so long, but everyone has assumed that someone else knew exactly why it was a problem. To my chagrin, NewSID has never really done anything useful and there’s no reason to miss it now that it’s retired.
Note that Sysprep resets other machine-specific state that, if duplicated, can cause problems for certain applications like Windows Server Update Services (WSUS), so Microsoft’s support policy will still require cloned systems to be made unique with Sysprep
令人有点惊讶的是,SID 重复问题这么长时间以来都没有受到质疑,但每个人都认为其他人确切地知道为什么会出现这个问题。令我懊恼的是,NewSID 从未真正做过任何有用的事情,既然它已经退役了,就没有理由错过它。请注意,Sysprep 会重置其他特定于计算机的状态,如果重复,可能会导致 Windows Server Update Services (WSUS) 等某些应用程序出现问题,因此 Microsoft 的支持策略仍然要求使用 Sysprep 使克隆系统具有唯一性