Published January 8, 2025
發布日期:2025 年 1 月 8 日
Every morning I get up and check what malicious packages my detector had found the night before. It’s like someone checking their fishing nets to see what fish they caught.
每天早上起床,我都會查看我的偵測器前一晚找到哪些惡意套件。這就像有人檢查漁網,看看捕到了什麼魚一樣。
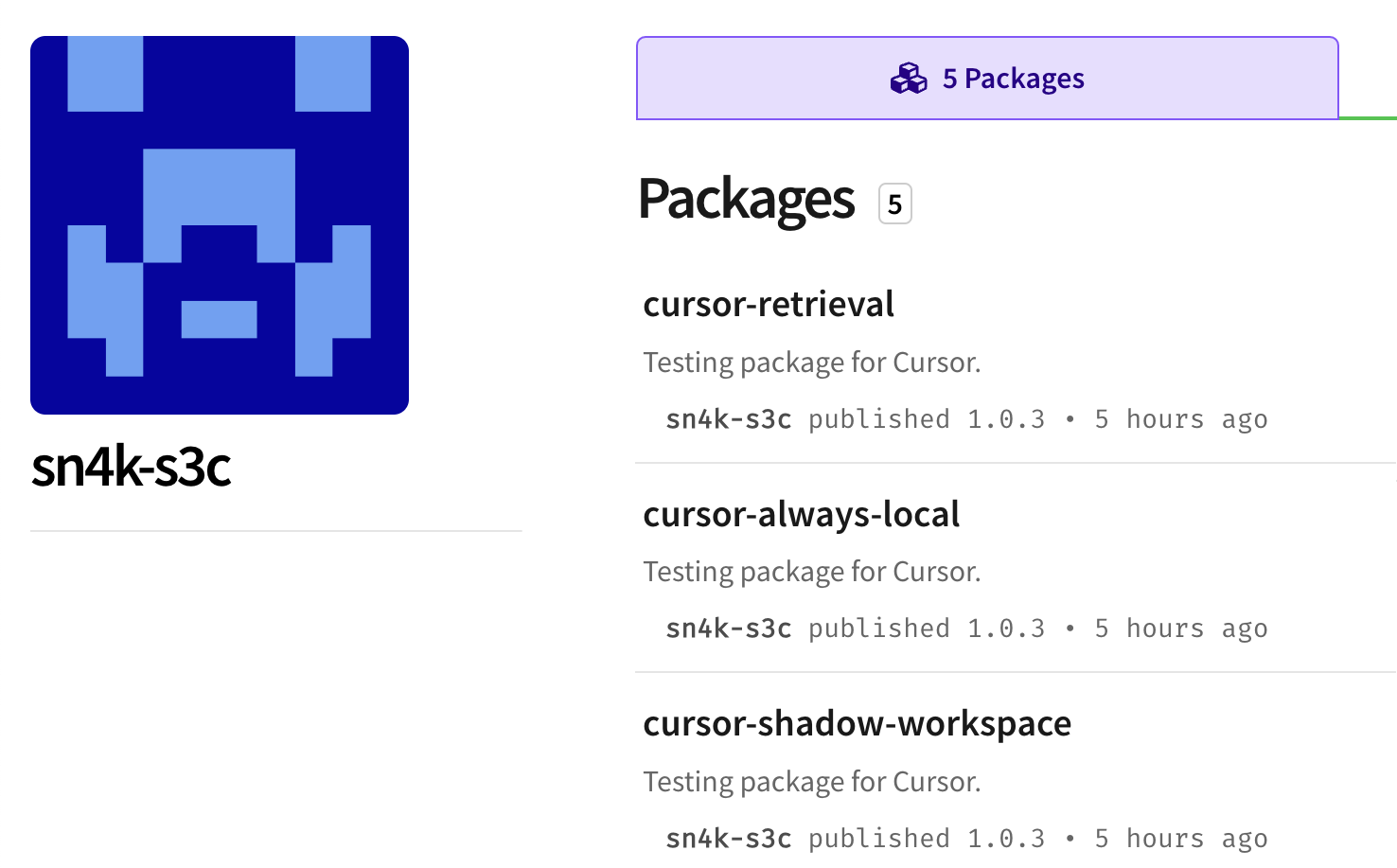
As I was looking at last nights malicious packages I noticed something strange: Someone from Snyk had deployed several packages to NPM. Even weirder, the names of those packages appeared to show they were targeting Cursor, the hot new AI coding company.
當我查看昨晚的惡意套件時,發現了一些奇怪的事情:Snyk 的某人已將幾個套件部署到 NPM。更奇怪的是,這些套件的名稱似乎顯示它們鎖定的是炙手可熱的新 AI 編碼公司 Cursor。
These packages were deployed by an NPM user named sn4k-s3c. The packages are named things like “cursor-retreival”, “cursor-always-local” and “cursor-shadow-workspace”.
這些套件是由名為 sn4k-s3c 的 NPM 使用者部署的。套件名稱像是「cursor-retreival」、「cursor-always-local」和「cursor-shadow-workspace」。
If you install any of these packages they will collect data about your system and send it to an attacker controlled web service.
如果你安裝任何這些套件,它們會收集你的系統資料並將其傳送給攻擊者控制的網路服務。
You can find the packages on NPM here: https://www.npmjs.com/~sn4k-s3c
你可以在這裡找到 NPM 上的這些套件:https://www.npmjs.com/~sn4k-s3c
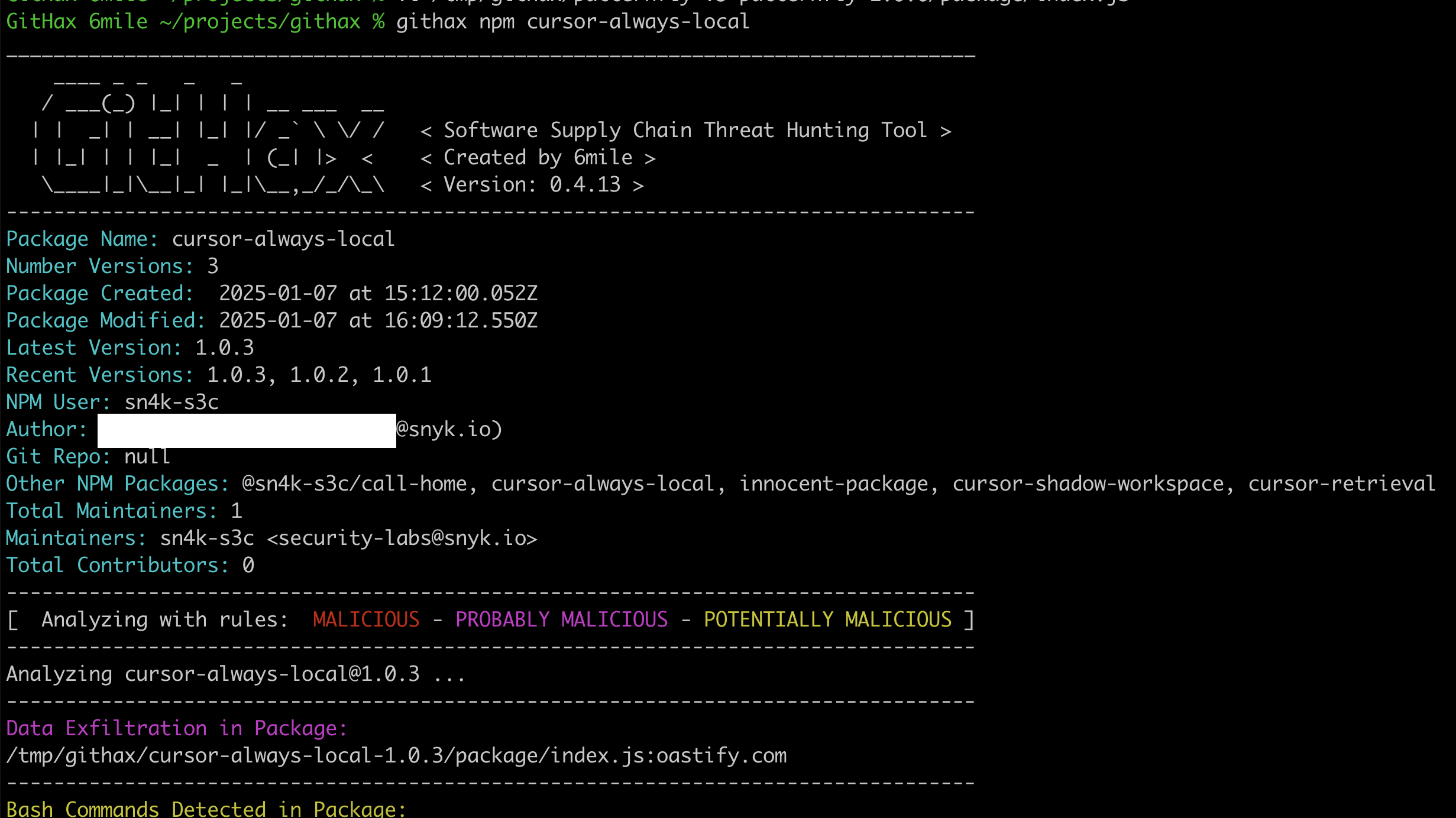
You can see in this screen shot that the package is grabbing the output of a env command which will include many configuration options for your system. Often things like AWS keys, NPM tokens, GitHub credentials and other sensitive variables are exposed by the env command, so guess what? The threat actor now has all those credentials too!
從這個螢幕截圖中可以看到,該套件正在擷取 env 命令的輸出,其中將包含許多系統組態選項。通常,AWS 金鑰、NPM 權杖、GitHub 憑證和其他敏感變數都會透過 env 命令公開,所以猜怎麼著?攻擊者現在也擁有所有這些憑證了!
You can see in the screenshot that the data is then exfiltrated to a website that the attacker owns.
從螢幕截圖中可以看到,資料隨後被洩露到攻擊者擁有的網站。
Now, typically, when we see packages like this, they are attempting to perform a dependency confusion attack on a specific company. I don’t know if Cursor.com has a bug bounty program or a specific background. Still, I would suspect that Cursor has several NPM private packages named “cursor-always-local”, “cursor-retrieval”, and “cursor-shadow-workspace”. The person who created these packages is probably hoping that Cursor employees accidentally install these public packages, which will send their data to the attacker-controlled web service.
通常,當我們看到這樣的套件時,它們通常企圖對特定公司發動相依性混淆攻擊。我不確定 Cursor.com 是否有漏洞賞金計畫或相關背景,但我懷疑 Cursor 有幾個名為「cursor-always-local」、「cursor-retrieval」和「cursor-shadow-workspace」的 NPM 私有套件。建立這些套件的人可能希望 Cursor 的員工不小心安裝這些公開套件,這將會將他們的資料傳送到攻擊者控制的網路服務。
Luckily, in addition to me seeing these files, the OpenSSF package analysis scanner identified these packages as malicious. OSV generated 3 malware advisories: MAL-2025-27, MAL-2025-28 and MAL-2025-29. You can see the malware advisories here: https://osv.dev/list?q=cursor&ecosystem=npm
幸運的是,除了我看到這些檔案之外,OpenSSF 套件分析掃描器也將這些套件識別為惡意軟體。OSV 生成了 3 個惡意軟體警示:MAL-2025-27、MAL-2025-28 和 MAL-2025-29。您可以在此處查看惡意軟體警示:https://osv.dev/list?q=cursor&ecosystem=npm
Who deployed these malicious packages?
誰部署了這些惡意套件?
Okay, we know what the packages do when installing them, and we think they target Cursor.com. Who would do this? Well, the answer is in the NPM package metadata.
好,我們知道安裝這些套件後會發生什麼事,而且我們認為它們鎖定的是 Cursor.com。誰會這麼做呢?答案就在 NPM 套件的 metadata 中。
The user who published the NPM package uses a snyk.io email address for the Snyk Security Labs team. This part of the metadata cannot be faked. The author field in the metadata specifically mentions an employee at Snyk. This part of the NPM package metadata can be faked, but since the publisher is a verified Snyk email, my guess is that this genuinely came from Snyk.
發布 NPM 套件的使用者使用 snyk.io 的電子郵件地址,這是 Snyk 安全實驗室團隊的地址。這部分的 metadata 無法偽造。metadata 中的作者欄位特別提到了 Snyk 的一位員工。這部分的 NPM 套件 metadata 可以偽造,但由於發布者是經過驗證的 Snyk 電子郵件,所以我猜測這確實來自 Snyk。
What can you do? 你能做些什麼?
I’ve alerted NPM but these packages haven’t been marked as malicious yet, so no security tool could protect you from these malicious packages. Unfortunately, that’s how most software supply chain security tools work: you have to know that a package is malicious before the tool can protect you.
我已向 NPM 發出警報,但這些套件尚未被標記為惡意軟體,因此沒有任何安全工具可以保護你免受這些惡意套件的侵害。不幸的是,大多數軟體供應鏈安全工具的工作方式就是這樣:你必須知道某個套件是惡意的,該工具才能保護你。
But in general, it’s a good idea not to install NPM packages blindly. If you know what to look for, there are definite signals that these packages are dodgy. All of these packages have just two files: package.json and index.js (or main.js). This is one of several flags that you can use to determine if a package is legit or not.
但一般來說,不要盲目安裝 NPM 套件是個好主意。如果你知道該尋找什麼,肯定有一些跡象表明這些套件可疑。所有這些套件只有兩個檔案:package.json 和 index.js(或 main.js)。這是你可以用來判斷套件是否合法的幾個標誌之一。
Hopefully, NPM will remove these packages soon.
希望 NPM 很快就會移除這些套件。
Paul McCarty
SourceCodeRed.com Security Research & Trainer
SourceCodeRed.com 資安研究與培訓師